Linux Implementation of Cobalt Strike Beacon Targeting Organizations Worldwide
Researchers on Monday took the wraps off a newly discovered Linux and Windows re-implementation of Cobalt
New SpookJS Attack Bypasses Google Chrome’s Site Isolation Protection
A newly discovered side-channel attack demonstrated on modern processors can be weaponized to successfully overcome Site
WhatsApp to Finally Let Users Encrypt Their Chat Backups in the Cloud
WhatsApp on Friday announced it will roll out support for end-to-end encrypted chat backups on the
Mēris Botnet Hit Russia’s Yandex With Massive 22 Million RPS DDoS Attack
Russian internet giant Yandex has been the target of a record-breaking distributed denial-of-service (DDoS) attack by
Moving Forward After CentOS 8 EOL
The Linux community was caught unprepared when, in December 2020, as part of a change in
Russian Ransomware Group REvil Back Online After 2-Month Hiatus
The operators behind the REvil ransomware-as-a-service (RaaS) staged a surprise return after a two-month hiatus following
3 Ways to Secure SAP SuccessFactors and Stay Compliant
The work-from-anywhere economy has opened up the possibility for your human resources team to source the
Latest Atlassian Confluence Flaw Exploited to Breach Jenkins Project Server
The maintainers of Jenkins—a popular open-source automation server software—have disclosed a security breach after unidentified threat
ProtonMail Shares Activist’s IP Address With Authorities Despite Its “No Log” Claims
End-to-end encrypted email service provider ProtonMail has drawn criticism after it ceded to a legal request
Microsoft Says Chinese Hackers Were Behind SolarWinds Serv-U SSH 0-Day Attack
Microsoft has shared technical details about a now-fixed, actively exploited critical security vulnerability affecting SolarWinds Serv-U
Apple Delays Plans to Scan Devices for Child Abuse Images After Privacy Backlash
Apple is temporarily hitting the pause button on its controversial plans to screen users’ devices for
This New Malware Family Using CLFS Log Files to Avoid Detection
Cybersecurity researchers have disclosed details about a new malware family that relies on the Common Log
New BrakTooth Flaws Leave Millions of Bluetooth-enabled Devices Vulnerable
A set of new security vulnerabilities has been disclosed in commercial Bluetooth stacks that could enable
[LIVE WEBINAR] How Lean Security Teams Can Improve Their Time to Response
Cybersecurity could be described as a marathon for security teams that spend most of their time
Attackers Can Remotely Disable Fortress Wi-Fi Home Security Alarms
New vulnerabilities have been discovered in Fortress S03 Wi-Fi Home Security System that could be potentially
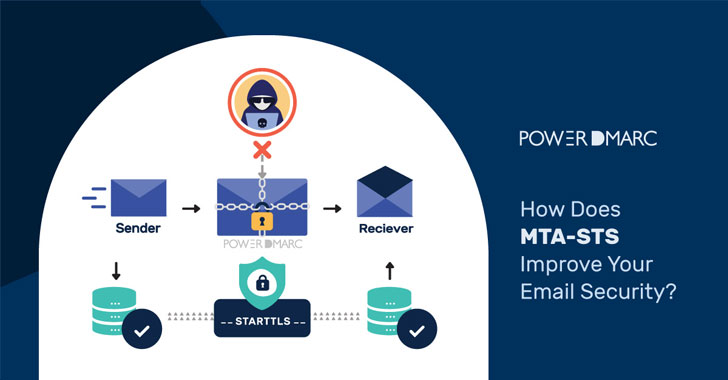
How Does MTA-STS Improve Your Email Security?
Simple Mail Transfer Protocol or SMTP has easily exploitable security loopholes. Email routing protocols were designed
Get Lifetime Access to 24 Professional Cybersecurity Certification Prep Courses
Not all heroes wear capes. Cybersecurity professionals are digital warriors who use their knowledge and skill
Kaseya Issues Patches for Two New 0-Day Flaws Affecting Unitrends Servers
U.S. technology firm Kaseya has released security patches to address two zero-day vulnerabilities affecting its Unitrends













![[LIVE WEBINAR] How Lean Security Teams Can Improve Their Time to Response](https://www.malaysiainternet.my/wp-content/uploads/2021/09/LIVE-WEBINAR-How-Lean-Security-Teams-Can-Improve-Their-Time.jpg)