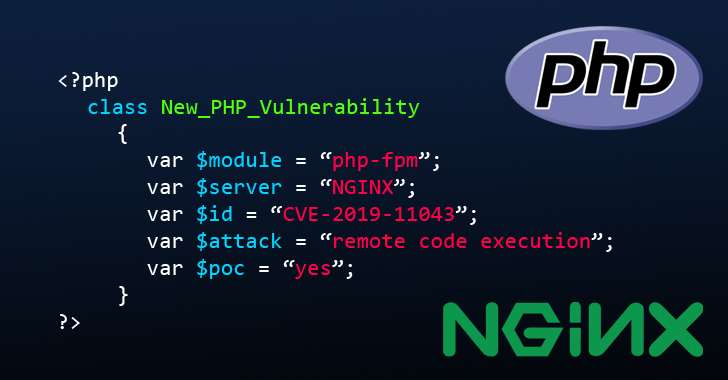
New PHP Flaw Could Let Attackers Hack Sites Running On Nginx Servers
If you’re running any PHP based website on NGINX server and have PHP-FPM feature enabled for
Verizon, AT&T, Sprint and T-Mobile to replace SMS with RCS Messaging in 2020
Mobile carriers in the United States will finally offer a universal cross-carrier communication standard for the
42 Adware Apps with 8 Million Downloads Traced Back to Vietnamese Student
First of all, if you have any of the below-listed apps installed on your Android device,
New Cache Poisoning Attack Lets Attackers Target CDN Protected Sites
A team of German cybersecurity researchers has discovered a new cache poisoning attack against web caching
Trust, but Verify: Digital Precaution helps Parents Protect Children
A new global survey from Kaspersky has found that when it comes to online security, some
NordVPN Breach FAQ – What Happened and What’s At Stake?
NordVPN, one of the most popular and widely used VPN services out there, yesterday disclosed details
Facebook Now Pays Hackers for Reporting Security Bugs in 3rd-Party Apps
Following a series of security mishaps and data abuse through its social media platform, Facebook today
A Comprehensive Guide On How to Protect Your Websites From Hackers
Humankind had come a long way from the time when the Internet became mainstream. What started
Feds Shut Down Largest Dark Web Child Abuse Site; South Korean Admin Arrested
The United States Department of Justice said today that they had arrested hundreds of criminals in
Microsoft to Reward Hackers for Finding Bugs in Open Source Election Software
Fair elections are the lifelines of democracy, but in recent years election hacking has become a
Chrome for Android Enables Site Isolation Security Feature for All Sites with Login
After enabling ‘Site Isolation’ security feature in Chrome for desktops last year, Google has now finally
Phorpiex Botnet Sending Out Millions of Sextortion Emails Using Hacked Computers
A decade-old botnet malware that currently controls over 450,000 computers worldwide has recently shifted its operations
Adobe Releases Out-of-Band Security Patches for 82 Flaws in Various Products
No, it’s not a patch Tuesday. It’s the third Tuesday of the month, and as The
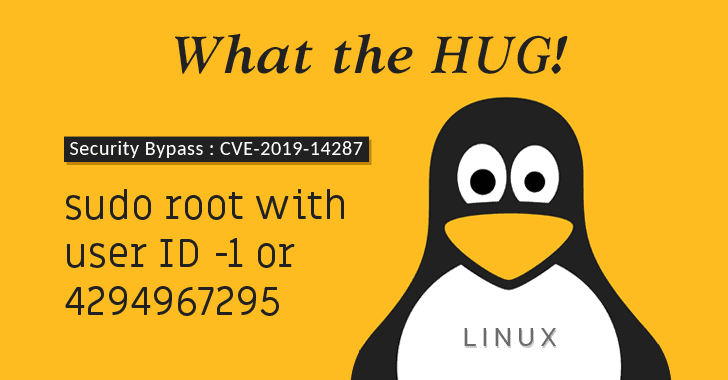
Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted
Attention Linux Users! A vulnerability has been discovered in Sudo—one of the most important, powerful, and
New Comic Videos Take CISO/Security Vendor Relationship to the Extreme
Today’s CISOs operate in an overly intensive environment. As the ones who are tasked with the
Hong Leong Bank Launches eToken with Biometric Recognition for Business
Hong Leong bank eToken has authentication technology built in, with additional first-in-market biometric facial recoginition technology
SIM Cards in 29 Countries Vulnerable to Remote Simjacker Attacks
Until now, I’m sure you all might have heard of the SimJacker vulnerability disclosed exactly a
UNIX Co-Founder Ken Thompson’s BSD Password Has Finally Been Cracked
A 39-year-old password of Ken Thompson, the co-creator of the UNIX operating system among, has finally