New High-Severity Vulnerability Reported in Pulse Connect Secure VPN
Ivanti, the company behind Pulse Secure VPN appliances, has published a security advisory for a high
What To Do When Your Business Is Hacked
As businesses move to a remote workforce, hackers have increased their activity to capitalize on new
Air India Hack Exposes Credit Card and Passport Info of 4.5 Million Passengers
India’s flag carrier airline, Air India, has disclosed a data breach affecting 4.5 million of its
FBI Analyst Charged With Stealing Counterterrorism and Cyber Threat Info
The U.S. Department of Justice (DoJ) indicted an employee of the Federal Bureau of Investigation (FBI)
Insurance Firm CNA Financial Reportedly Paid Hackers $40 Million in Ransom
U.S. insurance giant CNA Financial reportedly paid $40 million to a ransomware gang to recover access
23 Android Apps Expose Over 100,000,000 Users’ Personal Data
Misconfigurations in multiple Android apps leaked sensitive data of more than 100 million users, potentially making
DarkSide Ransomware Gang Extorted $90 Million from Several Victims in 9 Months
DarkSide, the hacker group behind the Colonial Pipeline ransomware attack earlier this month, received $90 million
How Apple Gave Chinese Government Access to iCloud Data and Censored Apps
In July 2018, when Guizhou-Cloud Big Data (GCBD) agreed to a deal with state-owned telco China
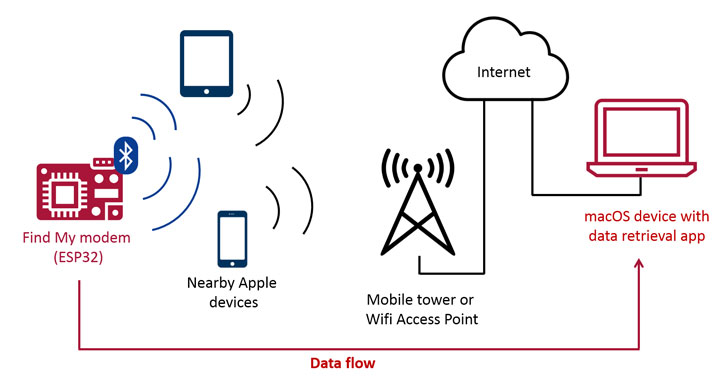
Apple’s Find My Network Can be Abused to Exfiltrate Data From Nearby Devices
Latest research has demonstrated a new exploit that enables arbitrary data to be uploaded from devices
Colonial Pipeline Paid Nearly $5 Million in Ransom to Cybercriminals
Colonial Pipeline on Thursday restored operations to its entire pipeline system nearly a week following a
Pakistan-Linked Hackers Added New Windows Malware to Its Arsenal
Cybercriminals with suspected ties to Pakistan continue to rely on social engineering as a crucial component
Hackers Using Microsoft Build Engine to Deliver Malware Filelessly
Threat actors are abusing Microsoft Build Engine (MSBuild) to filelessly deliver remote access trojans and password-stealing
Can Data Protection Systems Prevent Data At Rest Leakage?
Protection against insider risks works when the process involves controlling the data transfer channels or examining
Nearly All Wi-Fi Devices Are Vulnerable to New FragAttacks
Three design and multiple implementation flaws have been disclosed in IEEE 802.11 technical standard that undergirds
LIVE Webinar — The Rabbit Hole of Automation
The concept of automation has taken on a life of its own in recent years. The
Over 25% Of Tor Exit Relays Spied On Users’ Dark Web Activities
An unknown threat actor managed to control more than 27% of the entire Tor network exit
Ransomware Cyber Attack Forced the Largest U.S. Fuel Pipeline to Shut Down
Colonial Pipeline, which carries 45% of the fuel consumed on the U.S. East Coast, on Saturday
Facebook Will Limit Your WhatsApp Features For Not Accepting Privacy Policy
WhatsApp on Friday disclosed that it won’t deactivate accounts of users who don’t accept its new