Mozilla Says Google’s New Ad Tech—FLoC—Doesn’t Protect User Privacy
Google’s upcoming plans to replace third-party cookies with a less invasive ad targeted mechanism have a
Emerging Ransomware Targets Dozens of Businesses Worldwide
An emerging ransomware strain in the threat landscape claims to have breached 30 organizations in just
Crypto-Mining Attacks Targeting Kubernetes Clusters via Kubeflow Instances
Cybersecurity researchers on Tuesday disclosed a new large-scale campaign targeting Kubeflow deployments to run malicious cryptocurrency
Feds Secretly Ran a Fake Encrypted Chat App and Busted Over 800 Criminals
In a huge sting operation, the U.S. Federal Bureau of Investigation (FBI) and Australian Federal Police
Shifting the focus from reactive to proactive, with human-led secure coding
The same 10 software vulnerabilities have caused more security breaches in the last 20+ years than
TikTok Quietly Updated Its Privacy Policy to Collect Users’ Biometric Data
Popular short-form video-sharing service TikTok quietly revised its privacy policy in the U.S., allowing it to
GitHub Updates Policy to Remove Exploit Code When Used in Active Attacks
Code-hosting platform GitHub Friday officially announced a series of updates to the site’s policies that delve
Google to Let Android Users Opt-Out to Stop Ads From Tracking Them
Google is tightening the privacy practices that could make it harder for apps on Android phones
The Vulnerabilities of the Past Are the Vulnerabilities of the Future
Major software vulnerabilities are a fact of life, as illustrated by the fact that Microsoft has
Cybercriminals Hold $115,000-Prize Contest to Find New Cryptocurrency Hacks
A top Russian-language underground forum has been running a “contest” for the past month, calling on
Malware Can Use This Trick to Bypass Ransomware Defense in Antivirus Solutions
Researchers have disclosed significant security weaknesses in popular software applications that could be abused to deactivate
Your Amazon Devices to Automatically Share Your Wi-Fi With Neighbors
Starting June 8, Amazon will automatically enable a feature on your Alexa, Echo, or other Amazon
Chinese Cyber Espionage Hackers Continue to Target Pulse Secure VPN Devices
Cybersecurity researchers from FireEye unmasked additional tactics, techniques, and procedures (TTPs) adopted by Chinese threat actors
Researchers Demonstrate 2 New Hacks to Modify Certified PDF Documents
Cybersecurity researchers have disclosed two new attack techniques on certified PDF documents that could potentially enable
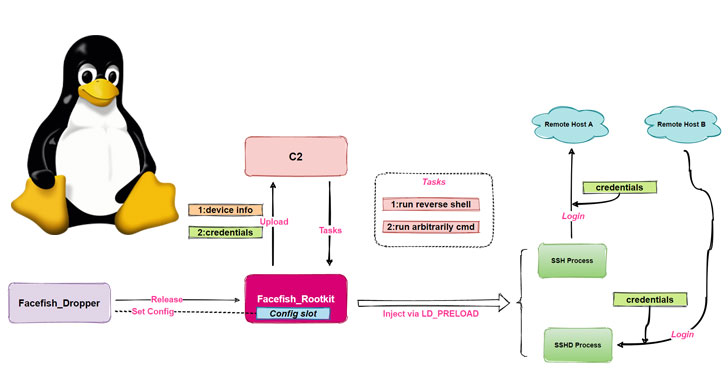
Researchers Warn of Facefish Backdoor Spreading Linux Rootkits
Cybersecurity researchers have disclosed a new backdoor program capable of stealing user login credentials, device information
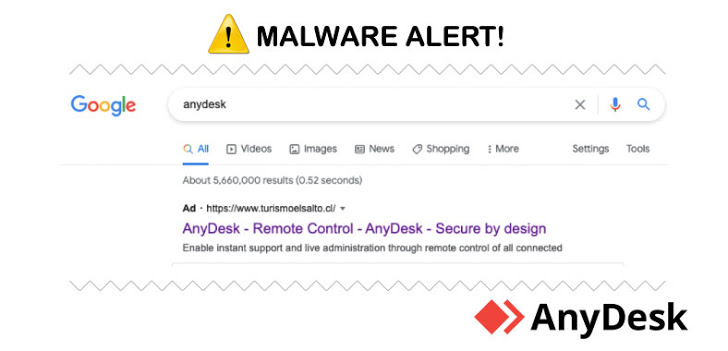
Malvertising Campaign On Google Distributed Trojanized AnyDesk Installer
Cybersecurity researchers on Wednesday publicized the disruption of a “clever” malvertising network targeting AnyDesk that delivered
Data Wiper Malware Disguised As Ransomware Targets Israeli Entities
Researchers on Tuesday disclosed a new espionage campaign that resorts to destructive data-wiping attacks targeting Israeli
New High-Severity Vulnerability Reported in Pulse Connect Secure VPN
Ivanti, the company behind Pulse Secure VPN appliances, has published a security advisory for a high