
As hybrid and remote work continue to be the norm in Southeast Asia (SEA), Kaspersky has foiled here over 47M Remote Desktop Protocol (RDP) attacks during the first six months of 2022.
The number of Bruteforce.Generic.RDP targeting remote workers in the region logged a total of 47,802,037 incidents from January to June this year. On average, Kaspersky solutions blocked 265,567 brute-force attacks in SEA daily.
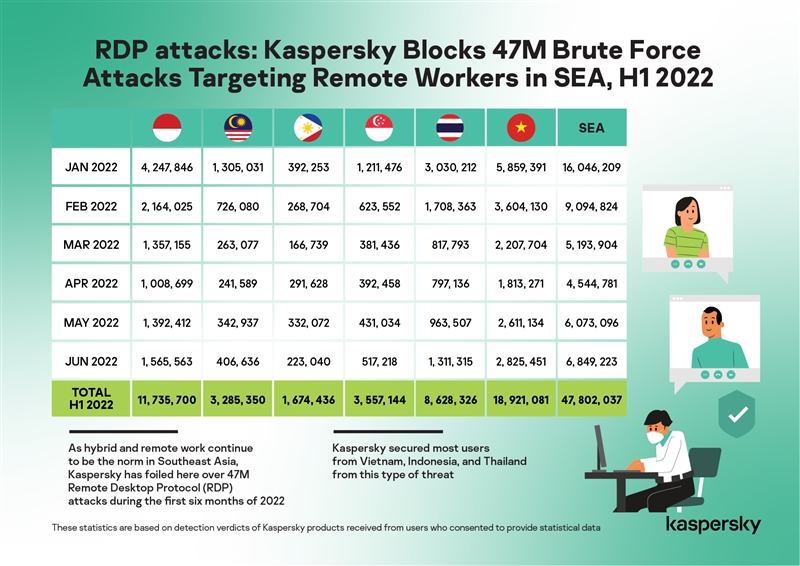
In this period, Kaspersky secured most users from Vietnam, Indonesia, and Thailand from this type of threat.
These statistics are based on detection verdicts of Kaspersky products received from users who consented to provide statistical data.
Remote Desktop Protocol (RDP) is Microsoft’s proprietary protocol, providing a user with a graphical interface to connect to another computer through a network. RDP is widely used by both system administrators and less-technical users to control servers and other PCs remotely.
A Bruteforce.Generic.RDP attack attempts to find a valid RDP login/password pair by systematically checking all possible passwords until the correct one is found.
A successful Bruteforce.Generic.RDP attack allows an attacker to gain remote access to the targeted host computer.
“Naturally, working from home or anywhere out of the office requires employees to log in to corporate resources remotely from their personal devices. One of the most common tools used for this purpose is RDP. Microsoft 365 is still the preferred software used by enterprises and SEA boasts of more than 680 million people, half of which are under 30 and are highly tech-savvy. So we see the use of this protocol to continue as remote working remains the norm and expect that malicious actors will continue their chase to compromise companies and organisations here through brute-force attacks,” says Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky.
While RDP attacks are not conceptually new, Kaspersky notes that cybercriminals exploit the recent trends and the remote and hybrid environment to target enterprises. Brute-force attacks on RDP are not new, but never before have so many employees used these protocols. That is likely the reason why they continue to be the primary focus for attackers in SEA.
While corporate and perimeter security remains important, the recent mass transition to remote or hybrid work has shown all too clearly that even the best corporate security cannot compensate for a lack of user awareness. Especially with 60% of companies allowing employees to use their own devices for work, businesses must train their staff in cybersecurity best practices, so that they are aware of the risks and understand how to work securely with corporate resources.
This cyber hygiene training must also be accompanied by changes in IT administration. IT needs to provide additional support to employees, making sure updates are applied on time and issues with connecting remotely are fixed promptly.
For many businesses, remote work is not a temporary solution. Many have already announced that, even after the pandemic subsides, work-from-home options and a hybrid model will become a permanent fixture of the employee experience.
“Moving forward, businesses have to rethink the way their corporate networks are organised. Since all machines are not located in the office and hence, not connected to the corporate network, adjustments need to be made to ensure endpoints stay secure and corporate resources are protected. Cybercriminals will always be ready to take advantage of disruptive current events. Fortunately, staying protected against an evolving set of cyber risks does not require any high-tech or advanced programming skills. It just requires a little knowledge of basic cyber safety rules,” adds Yeo.
Kaspersky experts also offer tips to help employers and businesses stay on top of any potential IT security issues and remain productive while staffs are working remotely or from home:
- Ensure your employees have all they need to securely work from home and know who to contact if they face an IT or security issue.
- Schedule basic security awareness training for your employees. This can be done online and cover essential practices, such as account and password management, email security, endpoint security, and web browsing.
- Take key data protection measures including switching on password protection, encrypting work devices, and ensuring data is backed up.
- Ensure devices, software, applications, and services are kept updated with the latest patches.
- Install proven protection software, such as Kaspersky Endpoint Security for Business, on all endpoints, including mobile devices, and switch on firewalls.
- Ensure you have access to the latest threat intelligence to bolster your protection solution.
- Double-check the protection available on mobile devices. For example, it should enable anti-theft capabilities such as remote device location, locking and wiping of data, screen locking, passwords, and biometric security features like Face ID or Touch ID, as well as enable application controls to ensure only approved applications are used by employees.
- In addition to physical endpoints, it is important to protect cloud workloads and virtual desktop infrastructure. As such, Kaspersky Hybrid Cloud Security protects hybrid infrastructure of physical and virtual endpoints, as well as cloud workloads whether running on premise, in a datacentre or in a public cloud. It supports integration with major cloud platforms, such as VMware, Citrix or Microsoft, and facilitates migration from physical to virtual desktops.
This article is written by Kaspersky.











