
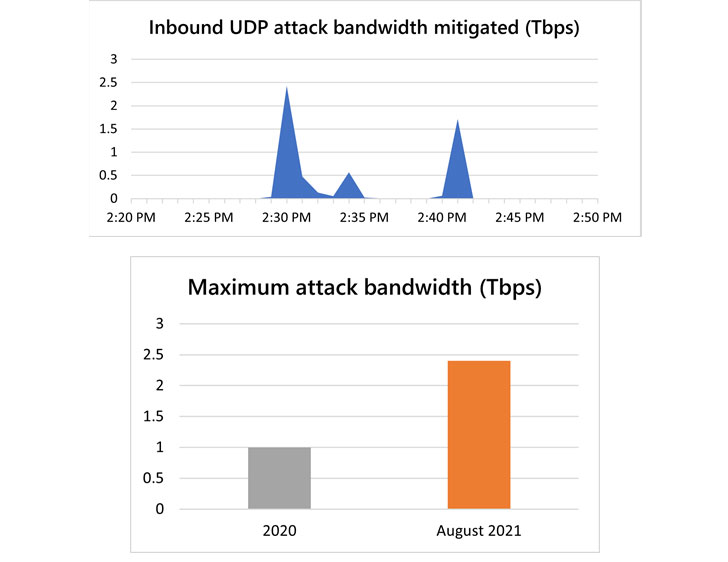
Microsoft on Monday revealed that its Azure cloud platform mitigated a 2.4 Tbps distributed denial-of-service (DDoS) attack in the last week of August targeting an unnamed customer in Europe, surpassing a 2.3 Tbps attack stopped by Amazon Web Services in February 2020.
“This is 140 percent higher than 2020’s 1 Tbps attack and higher than any network volumetric event previously detected on Azure,” Amir Dahan, senior program manager for Azure Networking, said in a post, calling it a “UDP reflection” lasting for about 10 minutes.

Reflected amplification attacks are a type of denial of service attacks wherein a threat actor takes advantage of the connectionless nature of UDP protocol with spoofed requests so as to overwhelm a target server or network with a flood of packets, causing disruption or rendering the server and its surrounding infrastructure unavailable.
The attack is said to have originated from a botnet of approximately 70,000 compromised devices primarily located across the Asia-Pacific region, such as Malaysia, Vietnam, Taiwan, Japan, and China, as well as the U.S.
Microsoft said it observed three short-lived bursts, each ramping up in seconds to terabit volumes…
http://feedproxy.google.com/~r/TheHackersNews/~3/ws0ovd_KIJI/microsoft-fended-off-record-24-tbps.html











