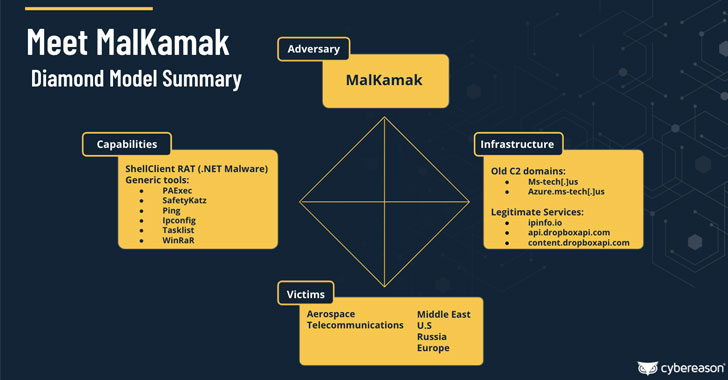
Details have emerged about a new cyber espionage campaign directed against the aerospace and telecommunications industries, primarily in the Middle East, with the goal of stealing sensitive information about critical assets, organizations’ infrastructure, and technology while remaining in the dark and successfully evading security solutions.
Boston-based cybersecurity company Cybereason dubbed the attacks “Operation Ghostshell,” pointing out the use of a previously undocumented and stealthy remote access trojan (RAT) called ShellClient that’s deployed as the main spy tool of choice. The first sign of the attacks was observed in July 2021 against a handpicked set of victims, indicating a highly targeted approach.
“The ShellClient RAT has been under ongoing development since at least 2018, with several iterations that introduced new functionalities, while it evaded antivirus tools and managed to remain undetected and publicly unknown,” researchers Tom Fakterman, Daniel Frank, Chen Erlich, and Assaf Dahan said in a technical deep dive published today.

Cybereason traced the roots of this threat back to at least November 6, 2018, previously operating as a standalone reverse shell…
http://feedproxy.google.com/~r/TheHackersNews/~3/CWLIwnoeDJI/iranian-hackers-abuse-dropbox-in.html