A new deceptive ad injection campaign has been found leveraging an ad blocker extension for Google Chrome and Opera web browsers to sneakily insert ads and affiliate codes on websites, according to new research from cybersecurity firm Imperva.
The findings come following the discovery of rogue domains distributing an ad injection script in late August 2021 that the researchers connected to an add-on called AllBlock. The extension has since been pulled from both the Chrome Web Store and Opera add-ons marketplaces.

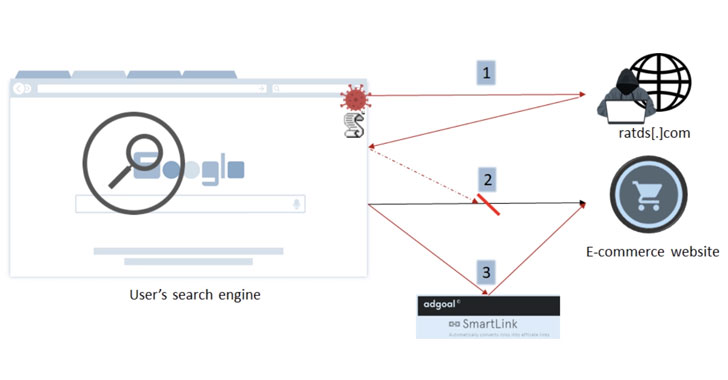
While AllBlock is designed to block ads legitimately, the JavaScript code is injected into every new tab opened on the browser. It works by identifying and sending all links in a web page — typically on search engine results pages — to a remote server, which responds back with a list of websites to replace the genuine links with, leading to a scenario where upon clicking a link, the victim is redirected to a different page.
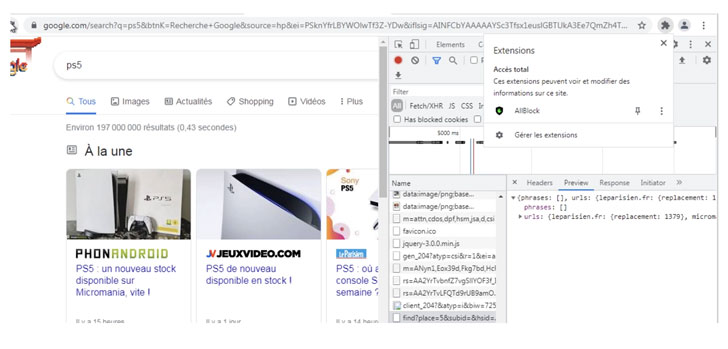
“When the user clicks on any modified links on the webpage, he will be redirected to an affiliate link,” Imperva researchers Johann Sillam and Ron Masas said. “Via this affiliate fraud, the attacker earns money when specific actions like…
http://feedproxy.google.com/~r/TheHackersNews/~3/3mHodx6X5ew/ad-blocking-chrome-extension-caught.html











