
Network security company SonicWall has addressed a critical security vulnerability affecting its Secure Mobile Access (SMA) 100 series appliances that can permit remote, unauthenticated attackers to gain administrator access on targeted devices remotely.
Tracked as CVE-2021-20034, the arbitrary file deletion flaw is rated 9.1 out of a maximum of 10 on the CVSS scoring system, and could allow an adversary to bypass path traversal checks and delete any file, causing the devices to reboot to factory default settings.
“The vulnerability is due to an improper limitation of a file path to a restricted directory potentially leading to arbitrary file deletion as ‘nobody,'” the San Jose-based firm noted in an advisory published Thursday. “There is no evidence that this vulnerability is being exploited in the wild.”
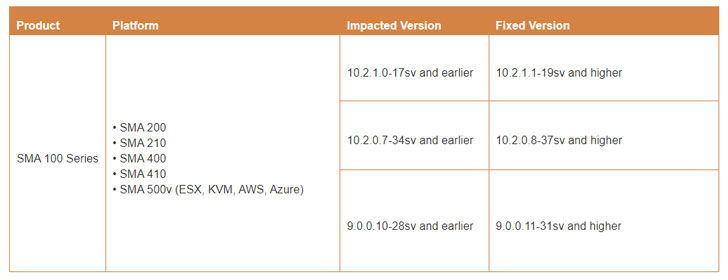
SonicWall credited Wenxu Yin of Alpha Lab, Qihoo 360, with reporting the security shortcoming, which impacts SMA 100 Series — SMA 200, SMA 210, SMA 400, SMA 410, and SMA 500v — running the following versions:
- 9.0.0.10-28sv and earlier
- 10.2.0.7-34sv and earlier
- 10.2.1.0-17sv and earlier

Given that there are no workarounds to remediate the attack vector and SonicWall…
http://feedproxy.google.com/~r/TheHackersNews/~3/XZ03V3AHhdQ/sonicwall-issues-patches-for-new.html











