A number of malicious samples have been created for the Windows Subsystem for Linux (WSL) with the goal of compromising Windows machines, highlighting a sneaky method that allows the operators to stay under the radar and thwart detection by popular anti-malware engines.
The “distinct tradecraft” marks the first instance where a threat actor has been found abusing WSL to install subsequent payloads.
“These files acted as loaders running a payload that was either embedded within the sample or retrieved from a remote server and was then injected into a running process using Windows API calls,” researchers from Lumen Black Lotus Labs said in a report published on Thursday.
Windows Subsystem for Linux, launched in August 2016, is a compatibility layer that’s designed to run Linux binary executables (in ELF format) natively on the Windows platform without the overhead of a traditional virtual machine or dual-boot setup.
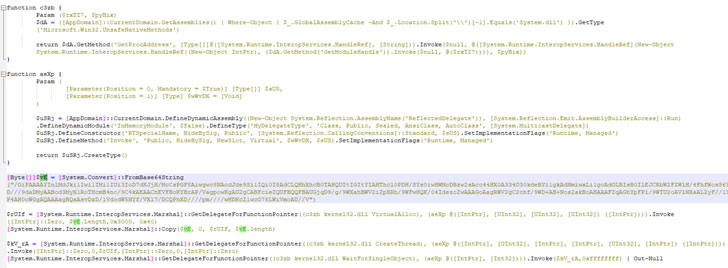
The earliest artifacts date back to May 3, 2021, with a series of Linux binaries uploaded every two to three weeks till August 22, 2021. Not only are the samples written in Python 3 and converted into an ELF executable with PyInstaller, but the files are also…
http://feedproxy.google.com/~r/TheHackersNews/~3/alb0Tv1cUr8/new-malware-targets-windows-subsystem.html