A new as-yet unpatched weakness in Apple’s iCloud Private Relay feature could be circumvented to leak users’ true IP addresses from iOS devices running the latest version of the operating system.
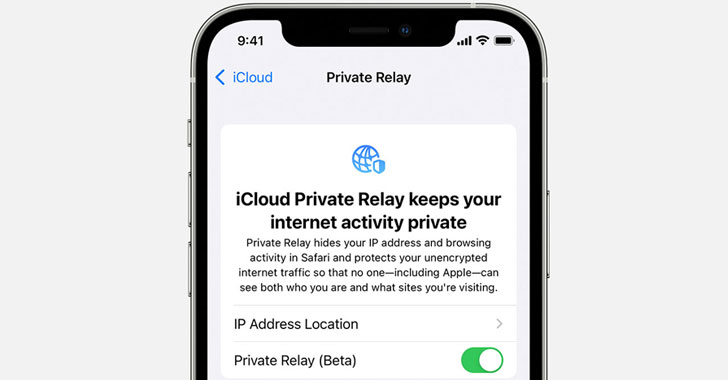
Introduced with iOS 15, which was officially released this week, iCloud Private Relay aims to improve anonymity on the web by employing a dual-hop architecture that effectively shields users’ IP address, location, and DNS requests from websites and network service providers.
It achieves this by routing users’ internet traffic on the Safari browser through two proxies in order to mask who’s browsing and where that data is coming from in what could be viewed as a simplified version of Tor.
However, the feature is available to iCloud+ subscribers running iOS 15 or macOS 12 Monterey and above.
“If you read the IP address from an HTTP request received by your server, you’ll get the IP address of the egress proxy,” FingerprintJS researcher Sergey Mostsevenko said. “Nevertheless, you can get the real client’s IP through WebRTC.”
WebRTC, short for Web Real-Time Communication, is an open-source initiative aimed at providing web browsers and mobile applications with real-time communication…
http://feedproxy.google.com/~r/TheHackersNews/~3/s4zOAPnxFu8/apples-new-icloud-private-relay-service.html











