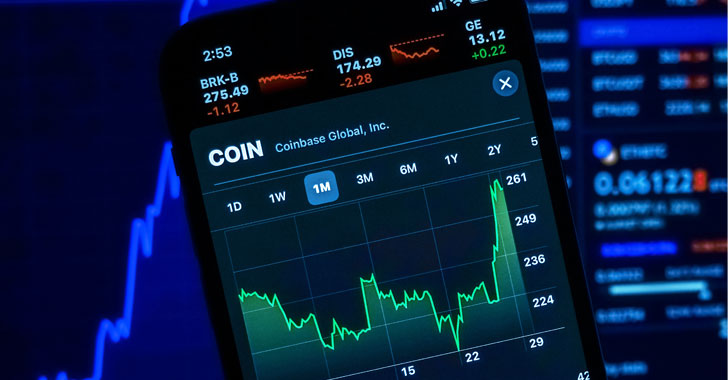
A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone, some of which have slipped past Apple’s on-device malware scanner and even signed by its own notarization service, highlighting the malicious software ongoing attempts to adapt and evade detection.
“AdLoad,” as the malware is known, is one of several widespread adware and bundleware loaders targeting macOS since at least 2017. It’s capable of backdooring an affected system to download and install adware or potentially unwanted programs (PUPs), as well as amass and transmit information about victim machines.

The new iteration “continues to impact Mac users who rely solely on Apple’s built-in security control XProtect for malware detection,” SentinelOne threat researcher Phil Stokes said in an analysis published last week. “As of today, however, XProtect arguably has around 11 different signatures for AdLoad [but] the variant used in this new campaign is undetected by any of those rules.”
The 2021 version of AdLoad latches on to persistence and executable names that use a different file extension pattern (.system or .service), enabling the…
http://feedproxy.google.com/~r/TheHackersNews/~3/AL44q59e3Wk/new-adload-variant-bypasses-apples.html