Simple Mail Transfer Protocol or SMTP has easily exploitable security loopholes. Email routing protocols were designed in a time when cryptographic technology was at a nascent stage (e.g., the de-facto protocol for email transfer, SMTP, is nearly 40 years old now), and therefore security was not an important consideration.
As a result, in most email systems encryption is still opportunistic, which implies that if the opposite connection does not support TLS, it gets rolled back to an unencrypted one delivering messages in plaintext.
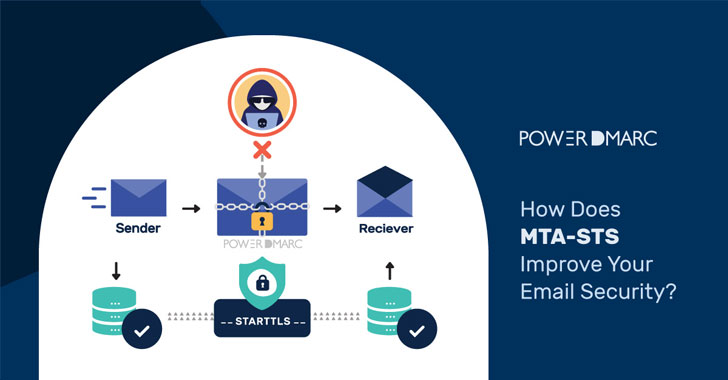
To mitigate SMTP security problems, MTA-STS (Mail Transfer Agent Strict Transport Security) is the recommended email authentication standard. It enforces TLS in order to allow MTAs to send emails securely. This means that it will only allow mail from MTAs that support TLS encryption, and it will only allow mail to go to MX hosts that support TLS encryption.
In case an encrypted connection cannot be negotiated between communicating SMTP servers, the email is not sent, instead of being sent over an unencrypted connection.
Analyzing the risks involved in transferring emails over an unencrypted SMTP connection
STARTTLS is a communication protocol…
http://feedproxy.google.com/~r/TheHackersNews/~3/OZCdxdVMp7s/how-does-mta-sts-improve-your-email.html











