
Unidentified threat actors are actively exploiting a critical authentication bypass vulnerability to hijack home routers as part of an effort to co-opt them to a Mirai-variant botnet used for carrying out DDoS attacks, merely two days after its public disclosure.
Tracked as CVE-2021-20090 (CVSS score: 9.9), the weakness concerns a path traversal vulnerability in the web interfaces of routers with Arcadyan firmware that could allow unauthenticated remote attackers to bypass authentication.

Disclosed by Tenable on August 3, the issue is believed to have existed for at least 10 years, affecting at least 20 models across 17 different vendors, including Asus, Beeline, British Telecom, Buffalo, Deutsche Telekom, Orange, Telstra, Telus, Verizon, and Vodafone.
Successful exploitation of the could enable an attacker to circumvent authentication barriers and potentially gain access to sensitive information, including valid request tokens, which could be used to make requests to alter router settings.
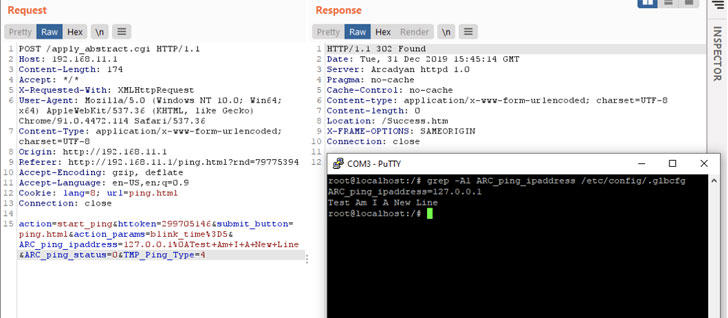
Juniper Threat Labs last week said it “identified some attack patterns that attempt to exploit this vulnerability in the wild coming from an IP address located in Wuhan, Hubei province,…
http://feedproxy.google.com/~r/TheHackersNews/~3/PSEnonM3NZY/hackers-exploiting-new-auth-bypass-bug.html












