
An Android malware that was observed abusing accessibility services in the device to hijack user credentials from European banking applications has morphed into an entirely new botnet as part of a renewed campaign that began in May 2021.
Italy’s CERT-AGID, in late January, disclosed details about Oscorp, a mobile malware developed to attack multiple financial targets with the goal of stealing funds from unsuspecting victims. Its features include the ability to intercept SMS messages and make phone calls and perform Overlay Attacks for more than 150 mobile applications by making use of lookalike login screens to siphon valuable data.

The malware was distributed through malicious SMS messages, with the attacks often conducted in real-time by posing as bank operators to dupe targets over the phone and surreptitiously gain access to the infected device via WebRTC protocol and ultimately conduct unauthorized bank transfers. While no new activities were reported since then, it appears that Oscorp may have staged a return after a temporary hiatus in the form of an Android botnet known as UBEL.
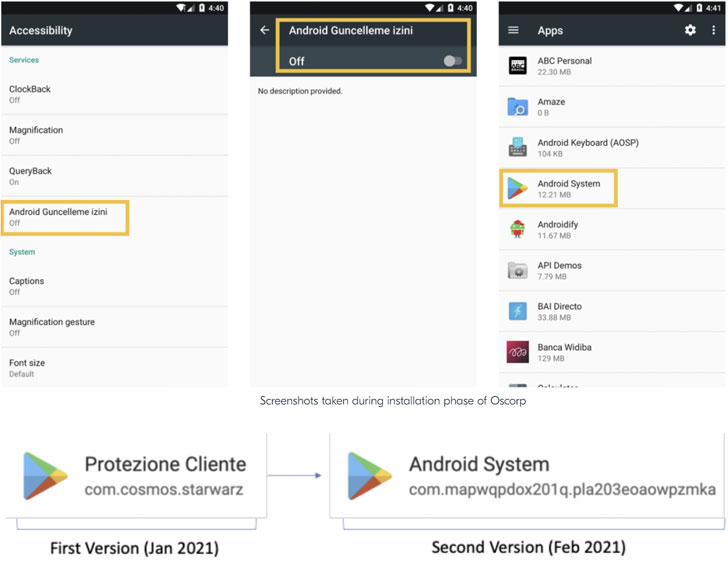
“By analyzing some related samples, we found multiple indicators linking Oscorp and UBEL…
http://feedproxy.google.com/~r/TheHackersNews/~3/EltJMRUOUGE/ubel-is-new-oscorp-android-credential.html













