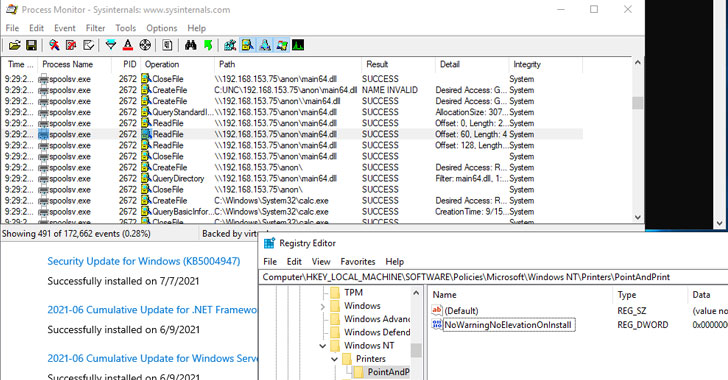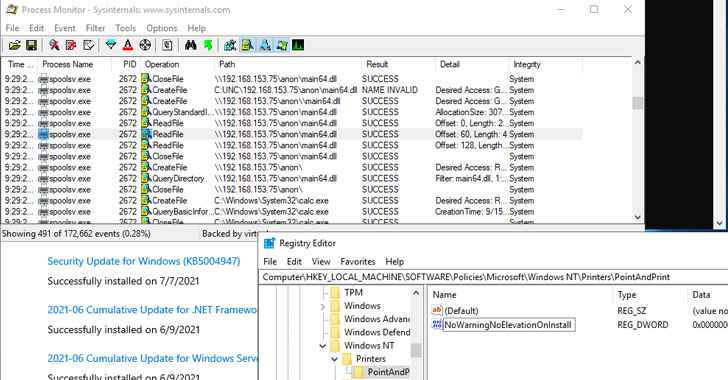
Even as Microsoft expanded patches for the so-called PrintNightmare vulnerability for Windows 10 version 1607, Windows Server 2012, and Windows Server 2016, it has come to light that the fix for the remote code execution exploit in the Windows Print Spooler service can be bypassed in certain scenarios, effectively defeating the security protections and permitting attackers to run arbitrary code on infected systems.
On Tuesday, the Windows maker issued an emergency out-of-band update to address CVE-2021-34527 (CVSS score: 8.8) after the flaw was accidentally disclosed by researchers from Hong Kong-based cybersecurity firm Sangfor late last month, at which point it emerged that the issue was different from another bug — tracked as CVE-2021-1675 — that was patched by Microsoft on June 8.

“Several days ago, two security vulnerabilities were found in Microsoft Windows’ existing printing mechanism,” Yaniv Balmas, head of cyber research at Check Point, told The Hacker News. “These vulnerabilities enable a malicious attacker to gain full control on all windows environments that enable printing.”
“These are mostly working stations but, at times, this relates to entire servers that…
http://feedproxy.google.com/~r/TheHackersNews/~3/6wJ1sNG2UPg/microsofts-emergency-patch-fails-to.html