

An adversary known for its watering hole attacks against government entities has been linked to a slew of newly detected intrusions targeting various organizations in Central Asia and the Middle East.
The malicious activity, collectively named “EmissarySoldier,” has been attributed to a threat actor called LuckyMouse, and is said to have happened in 2020 with the goal of obtaining geopolitical insights in the region. The attacks involved deploying a toolkit dubbed SysUpdate (aka Soldier) in a number of breached organizations, including government and diplomatic agencies, telecom providers, a TV media company, and a commercial bank.

LuckyMouse, also referred to as APT27 and Emissary Panda, is a sophisticated cyberespionage group that has a history of breaching multiple government networks in Central Asia and the Middle East. The actor has also been linked to cyberattacks aimed at transnational organizations such as the International Civil Aviation Organization (ICAO) in 2019 and recently attracted attention for exploiting ProxyLogon flaws to compromise the email server of a governmental entity in the Middle East.
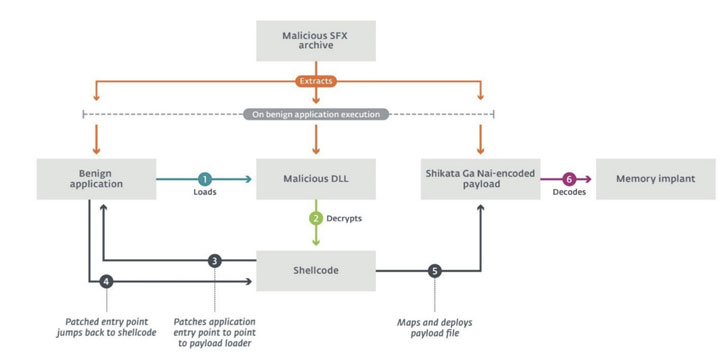
EmissarySoldier is only the latest in a series of surveillance…
http://feedproxy.google.com/~r/TheHackersNews/~3/Y7CPVO3mJQI/luckymouse-hackers-target-banks.html











