

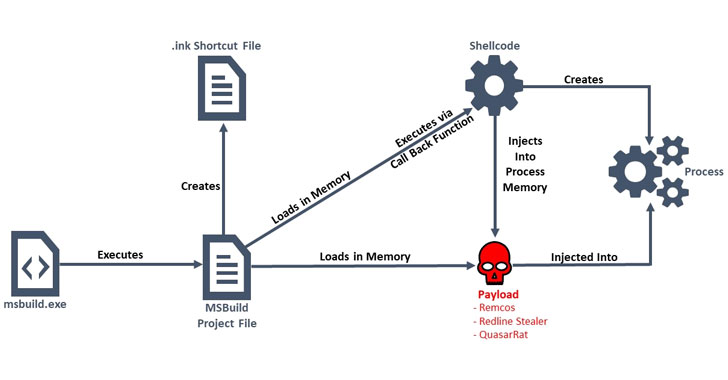
Threat actors are abusing Microsoft Build Engine (MSBuild) to filelessly deliver remote access trojans and password-stealing malware on targeted Windows systems.
The actively ongoing campaign is said to have emerged last month, researchers from cybersecurity firm Anomali said on Thursday, adding the malicious build files came embedded with encoded executables and shellcode that deploy backdoors, allowing the adversaries to take control of the victims’ machines and steal sensitive information.
MSBuild is an open-source build tool for .NET and Visual Studio developed by Microsoft that allows for compiling source code, packaging, testing, deploying applications.

In using MSBuild to filelessly compromise a machine, the idea is to stay under the radar and thwart detection, as such malware makes use of a legitimate application to load the attack code into memory, thereby leaving no traces of infection on the system and giving attackers a high level of stealth.
As of writing, only two security vendors flag one of the MSBuild .proj files (“vwnfmo.lnk”) as malicious, while a second sample (“72214c84e2.proj”) uploaded to VirusTotal on April 18 remains undetected by every anti-malware…
http://feedproxy.google.com/~r/TheHackersNews/~3/I2E879je8Hc/hackers-using-microsoft-build-engine-to.html











