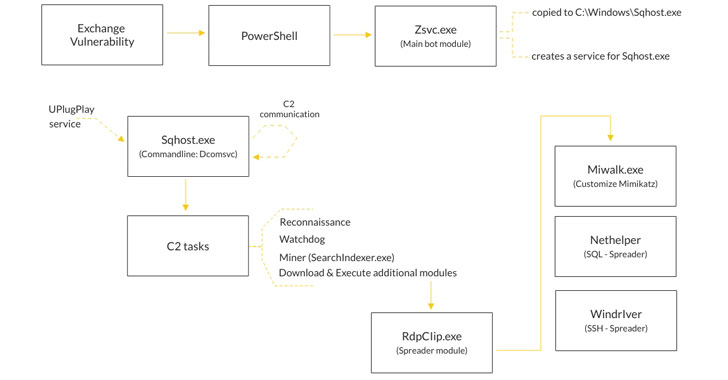
Attackers are exploiting the ProxyLogon Microsoft Exchange Server flaws to co-opt vulnerable machines to a cryptocurrency botnet named Prometei, according to new research.
“Prometei exploits the recently disclosed Microsoft Exchange vulnerabilities associated with the HAFNIUM attacks to penetrate the network for malware deployment, credential harvesting and more,” Boston-based cybersecurity firm Cybereason said in an analysis summarizing its findings.
First documented by Cisco Talos in July 2020, Prometei is a multi-modular botnet, with the actor behind the operation employing a wide range of specially-crafted tools and known exploits such as EternalBlue and BlueKeep to harvest credentials, laterally propagate across the network and “increase the amount of systems participating in its Monero-mining pool.”

“Prometei has both Windows-based and Linux-Unix based versions, and it adjusts its payload based on the detected operating system, on the targeted infected machines when spreading across the network,” Cybereason senior threat researcher Lior Rochberger said, adding it’s “built to interact with four different command-and-control (C2) servers which strengthens the botnet’s…
http://feedproxy.google.com/~r/TheHackersNews/~3/fzitt_8-kGM/prometei-botnet-exploiting-unpatched.html













