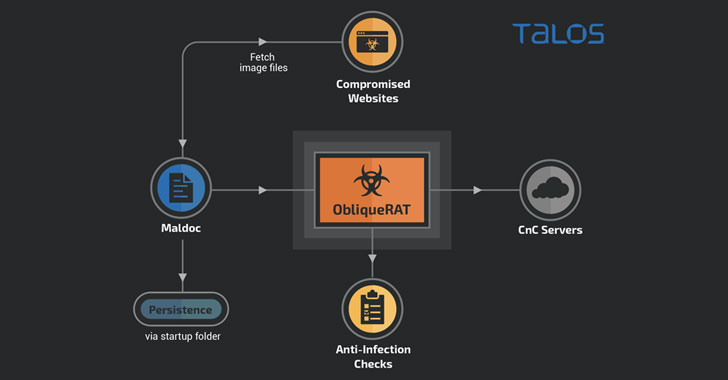
Cybercriminals are now deploying remote access Trojans (RATs) under the guise of seemingly innocuous images hosted on infected websites, once again highlighting how threat actors quickly change tactics when their attack methods are discovered and exposed publicly.
New research released by Cisco Talos reveals a new malware campaign targeting organizations in South Asia that utilize malicious Microsoft Office documents forged with macros to spread a RAT that goes by the name of ObliqueRAT.
First documented in February 2020, the malware has been linked to a threat actor tracked as Transparent Tribe (aka Operation C-Major, Mythic Leopard, or APT36), a highly prolific group allegedly of Pakistani origin known for its attacks against human rights activists in the country as well as military and government personnel in India.
While the ObliqueRAT modus operandi previously overlapped with another Transparent Tribe campaign in December 2019 to disseminate CrimsonRAT, the new wave of attacks differs in two crucial ways.
In addition to making use of a completely different macro code to download and deploy the RAT payload, the operators of the campaign have also updated the delivery…
http://feedproxy.google.com/~r/TheHackersNews/~3/XRIhZP_4QBk/hackers-now-hiding-obliquerat-payload.html












