New details have emerged about a vast network of rogue extensions for Chrome and Edge browsers that were found to hijack clicks to links in search results pages to arbitrary URLs, including phishing sites and ads.
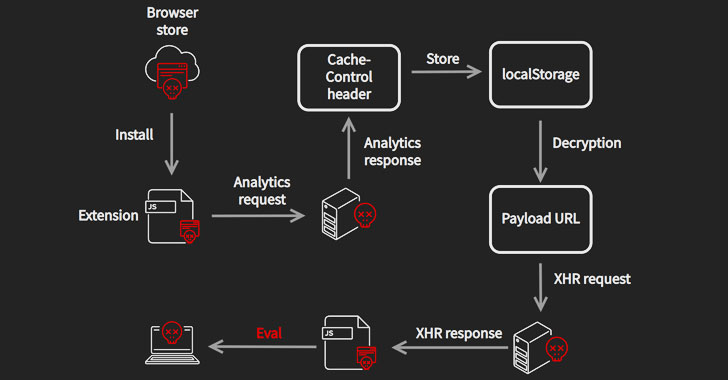
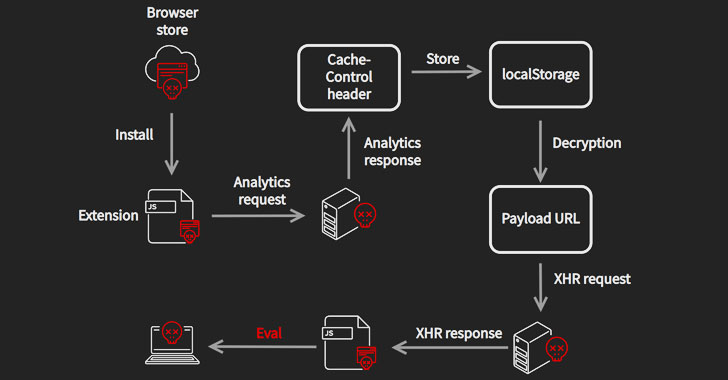
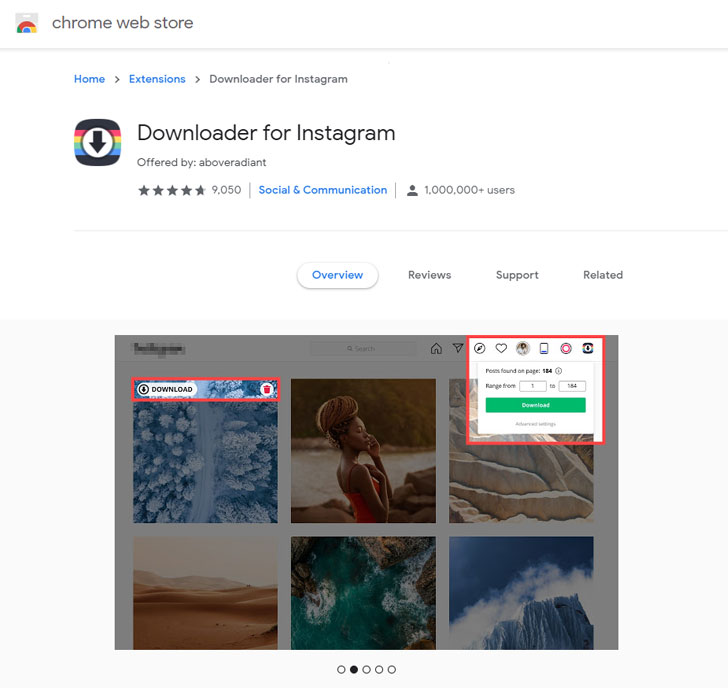
Collectively called “CacheFlow” by Avast, the 28 extensions in question — including Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock — made use of a sneaky trick to mask its true purpose: Leverage Cache-Control HTTP header as a covert channel to retrieve commands from an attacker-controlled server.
All the backdoored browser add-ons have been taken down by Google and Microsoft as of December 18, 2020, to prevent more users from downloading them from the official stores.

According to telemetry data gathered by the firm, the top three infected countries were Brazil, Ukraine, and France, followed by Argentina, Spain, Russia, and the U.S.
The CacheFlow sequence began when unsuspecting users downloaded one of the extensions in their browsers that, upon installation, sent out analytics requests resembling Google Analytics to a remote server, which then beamed back a specially-crafted Cache-Control header containing hidden…
http://feedproxy.google.com/~r/TheHackersNews/~3/o6KxwsBhziA/over-dozen-chrome-extensions-caught.html











