
UAE and Kuwait government agencies are targets of a new cyberespionage campaign potentially carried out by Iranian threat actors, according to new research.
Attributing the operation to be the work of Static Kitten (aka MERCURY or MuddyWater), Anomali said the “objective of this activity is to install a remote management tool called ScreenConnect (acquired by ConnectWise 2015) with unique launch parameters that have custom properties,” with malware samples and URLs masquerading as the Ministry of Foreign Affairs (MOFA) of Kuwait and the UAE National Council.

Since its origins in 2017, MuddyWater has been tied to a number of attacks primarily against Middle Eastern nations, actively exploiting Zerologon vulnerability in real-world attack campaigns to strike prominent Israeli organizations with malicious payloads.
The state-sponsored hacking group is believed to be working at the behest of Iran’s Islamic Republic Guard Corps, the country’s primary intelligence and military service.
Anomali said it spotted two separate lure ZIP files hosted on Onehub that claimed to contain a report on relations between Arab countries and Israel or a file relating to scholarships.
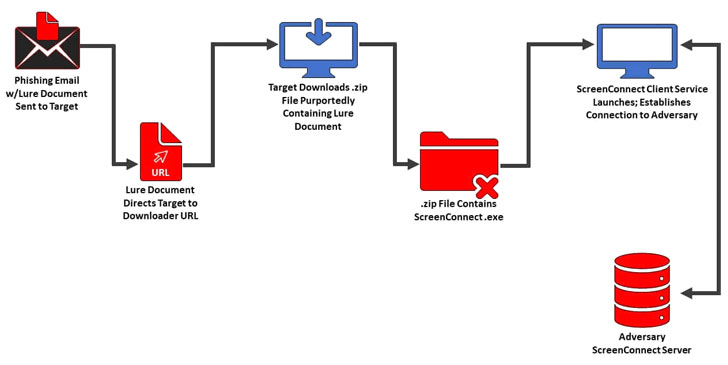
“The URLs…
http://feedproxy.google.com/~r/TheHackersNews/~3/jyqjJugp1-g/iranian-hackers-utilize-screenconnect.html












