An evolving phishing campaign observed at least since May 2020 has been found to target high-ranking company executives across manufacturing, real estate, finance, government, and technological sectors with the goal of obtaining sensitive information.
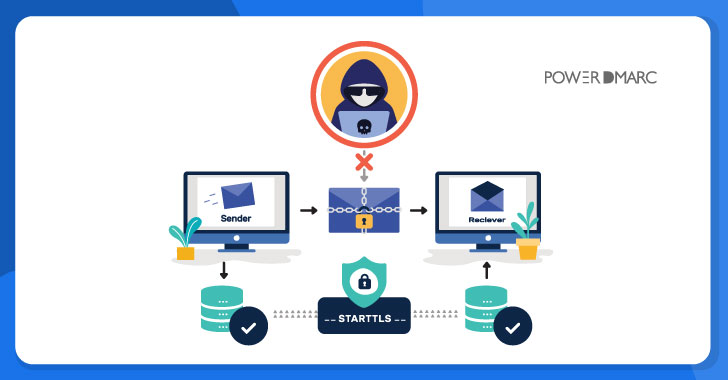
The campaign hinges on a social engineering trick that involves sending emails to potential victims containing fake Office 365 password expiration notifications as lures. The messages also include an embedded link to retain the same password that, when clicked, redirects users to a phishing page for credential harvesting.
“The attackers target high profile employees who may not be as technically or cybersecurity savvy, and may be more likely to be deceived into clicking on malicious links,” Trend Micro researchers said in a Monday analysis.

“By selectively targeting C-level employees, the attacker significantly increases the value of obtained credentials as they could lead to further access to sensitive personal and organizational information, and used in other attacks.”

According to the researchers, the targeted email addresses were mostly collected from LinkedIn, while noting that the attackers could have purchased such…
http://feedproxy.google.com/~r/TheHackersNews/~3/HuwFrzJ502Y/targeted-phishing-attacks-target-high.html