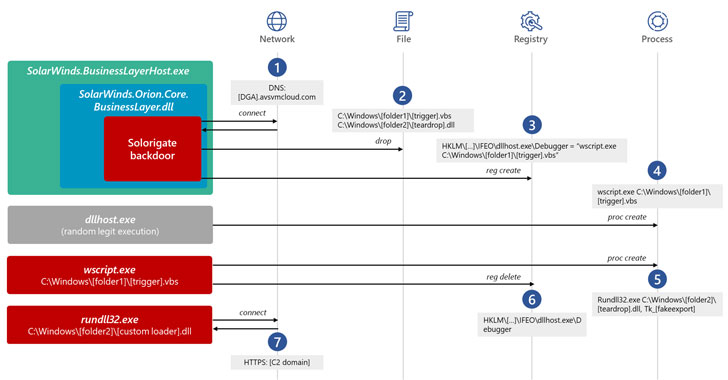
Microsoft on Wednesday shared more specifics about the tactics, techniques, and procedures (TTPs) adopted by the attackers behind the SolarWinds hack to stay under the radar and avoid detection, as cybersecurity companies work towards getting a “clearer picture” of one of the most sophisticated attacks in recent history.
Calling the threat actor “skillful and methodic operators who follow operations security (OpSec) best practices,” the company said the attackers went out of their way to ensure that the initial backdoor (Sunburst aka Solorigate) and the post-compromise implants (Teardrop and Raindrop) are separated as much as possible so as to hinder efforts to spot their malicious activity.
“The attackers behind Solorigate are skilled campaign operators who carefully planned and executed the attack, remaining elusive while maintaining persistence,” researchers from Microsoft 365 Defender Research Team, Microsoft Threat Intelligence Center (MSTIC), and Microsoft Cyber Defense Operations Center (CDOC) said.
While the exact identity of the group tracked as StellarParticle (CrowdStrike), UNC2452 (FireEye), SolarStorm (Palo Alto Unit 42), and Dark Halo (Volexity) remain unknown…
http://feedproxy.google.com/~r/TheHackersNews/~3/dtXPu-a78_E/heres-how-solarwinds-hackers-stayed.html