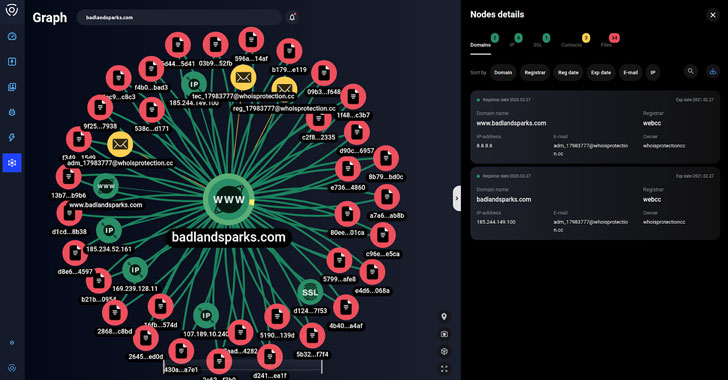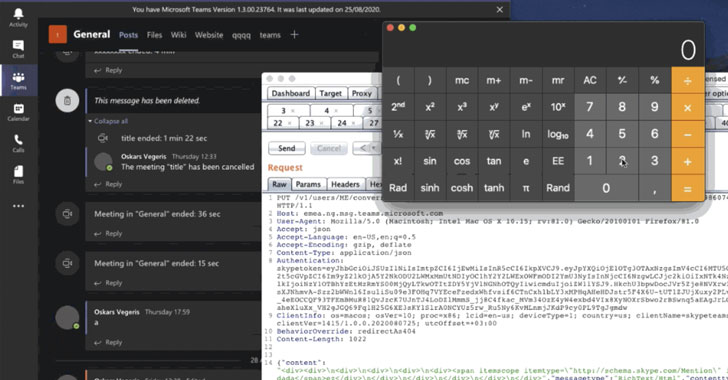
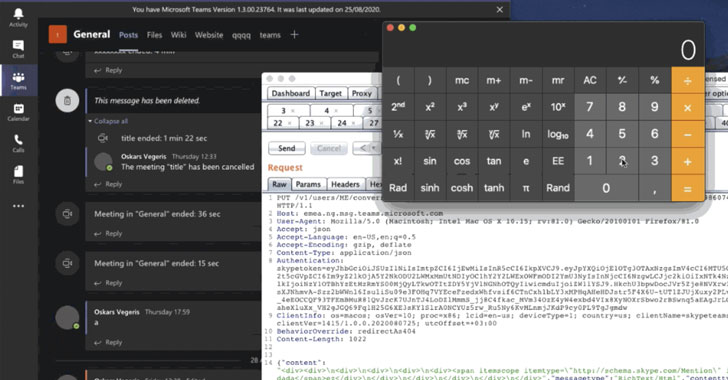
A zero-click remote code execution (RCE) bug in Microsoft Teams desktop apps could have allowed an adversary to execute arbitrary code by merely sending a specially-crafted chat message and compromise a target’s system.
The issues were reported to the Windows maker by Oskars Vegeris, a security engineer from Evolution Gaming, on August 31, 2020, before they were addressed at the end of October.
Microsoft did not assign a CVE to this vulnerability, stating “it’s currently Microsoft’s policy to not issue CVEs on products that automatically updates without user’s interaction.”
“No user interaction is required, exploit executes upon seeing the chat message,” Vegeris explained in a technical write-up.
The result is a “complete loss of confidentiality and integrity for end users — access to private chats, files, internal network, private keys and personal data outside MS Teams,” the researcher added.
Worse, the RCE is cross-platform — affecting Microsoft Teams for Windows (v1.3.00.21759), Linux (v1.3.00.16851), macOS (v1.3.00.23764), and the web (teams.microsoft.com) — and could be made wormable, meaning it could be propagated by automatically reposting the malicious payload…
http://feedproxy.google.com/~r/TheHackersNews/~3/Ff5kgbod0XI/zero-click-wormable-rce-vulnerability.html