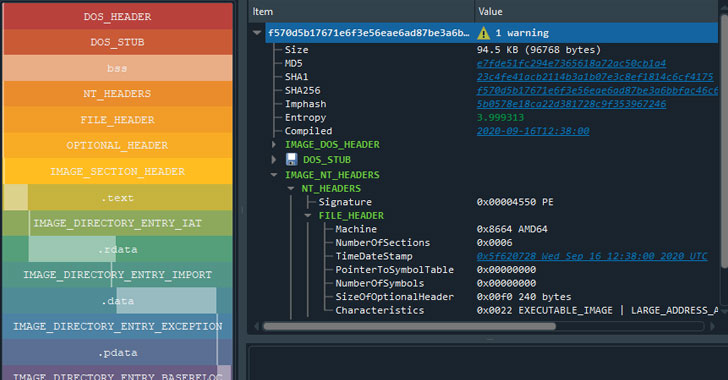
A relatively new ransomware strain behind a series of breaches on corporate networks has developed new capabilities that allow it to broaden the scope of its targeting and evade security software—as well as with ability for its affiliates to launch double extortion attacks.
The MountLocker ransomware, which only began making the rounds in July 2020, has already gained notoriety for stealing files before encryption and demanding ransom amounts in the millions to prevent public disclosure of stolen data, a tactic known as double extortion.
“The MountLocker Operators are clearly just warming up. After a slow start in July they are rapidly gaining ground, as the high-profile nature of extortion and data leaks drive ransom demands ever higher,” researchers from BlackBerry Research and Intelligence Team said.
“MountLocker affiliates are typically fast operators, rapidly exfiltrating sensitive documents and encrypting them across key targets in a matter of hours.”
MountLocker also joins the likes of other ransomware families like Maze (which shut down its operations last month) that operate a website on the dark web to name and shame victims and supply links to leaked data.
To…
http://feedproxy.google.com/~r/TheHackersNews/~3/hcEDQk_f12A/mount-locker-ransomware-offering-double.html