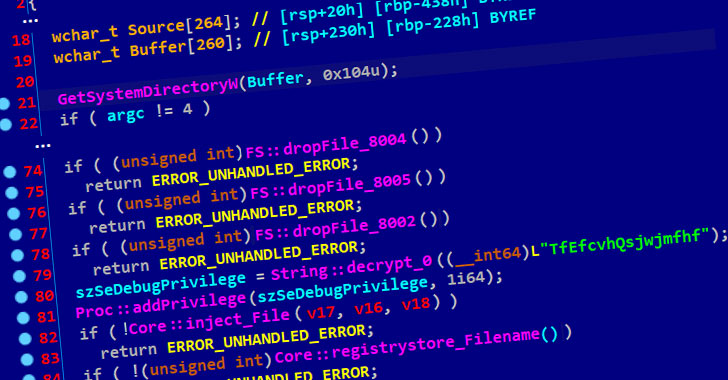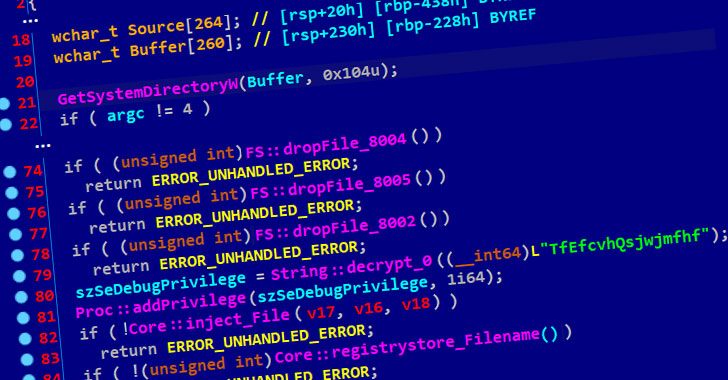
Cybersecurity researchers took the wraps off a novel supply chain attack in South Korea that abuses legitimate security software and stolen digital certificates to distribute remote administration tools (RATs) on target systems.
Attributing the operation to the Lazarus Group, also known as Hidden Cobra, Slovak internet security company ESET said the state-sponsored threat actor leveraged the mandatory requirement that internet users in the country must install additional security software in order to avail Internet banking and essential government services.
The attack, while limited in scope, exploits WIZVERA VeraPort, which is billed as a “program designed to integrate and manage internet banking-related installation programs,” such as digital certificates issued by the banks to individuals and businesses to secure all transactions and process payments.
The development is the latest in a long history of espionage attacks against victims in South Korea, including Operation Troy, DDoS attacks in 2011, and against banking institutions and cryptocurrency exchanges over the last decade.
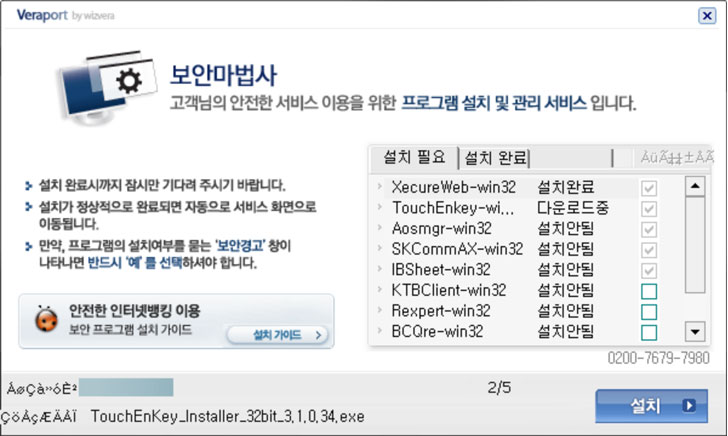
Aside from using the aforementioned technique of installing security software in order to…
http://feedproxy.google.com/~r/TheHackersNews/~3/0DGOd787cuc/trojanized-security-software-hits-south.html