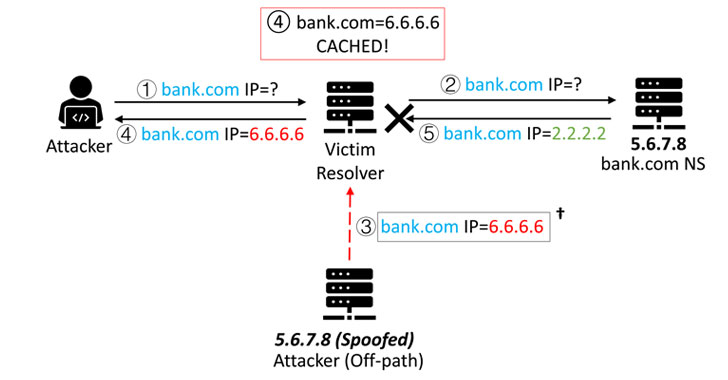
A group of academics from the University of California and Tsinghua University has uncovered a series of critical security flaws that could lead to a revival of DNS cache poisoning attacks.
Dubbed “SAD DNS attack” (short for Side-channel AttackeD DNS), the technique makes it possible for a malicious actor to carry out an off-path attack, rerouting any traffic originally destined to a specific domain to a server under their control, thereby allowing them to eavesdrop and tamper with the communications.
“This represents an important milestone — the first weaponizable network side channel attack that has serious security impacts,” the researchers said. “The attack allows an off-path attacker to inject a malicious DNS record into a DNS cache.”
Tracked as CVE-2020-25705, the findings were presented at the ACM Conference on Computer, and Communications Security (CCS ’20) held this week.
The flaw affects operating systems Linux 3.18-5.10, Windows Server 2019 (version 1809) and newer, macOS 10.15 and newer, and FreeBSD 12.1.0 and newer.
DNS Forwarders Become New Attack Surface
DNS resolvers typically cache responses to IP address queries for a specific period as a means to improve…
http://feedproxy.google.com/~r/TheHackersNews/~3/t9h9ZcYke_Q/sad-dns-new-flaws-re-enable-dns-cache.html
