Cybersecurity researchers today took the wraps off an on-going cyber fraud operation led by hackers in Gaza, West Bank, and Egypt to compromise VoIP servers of more than 1,200 organizations across 60 countries over the past 12 months.
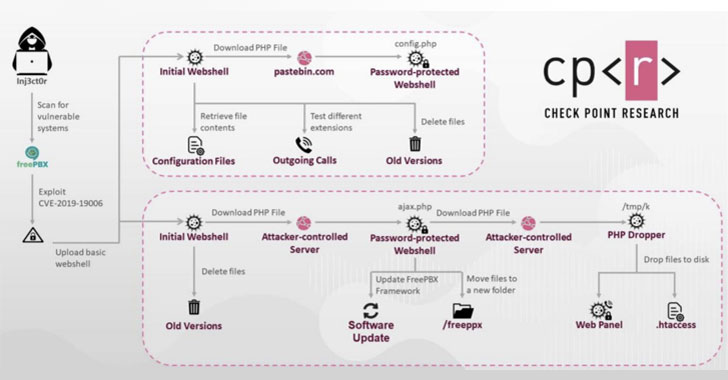
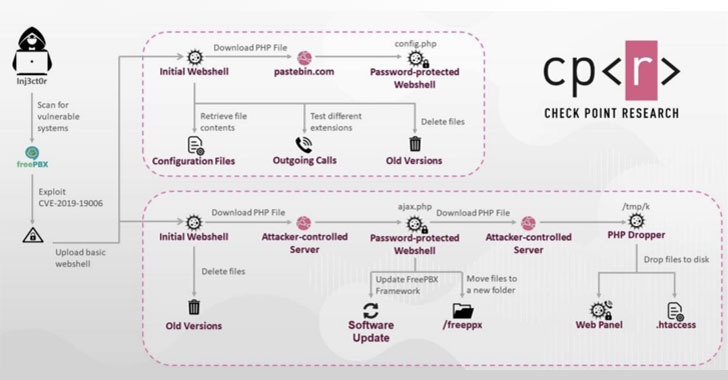
According to findings published by Check Point Research, the threat actors — believed to be located in the Palestinian Gaza Strip — have targeted Sangoma PBX, an open-sourced user interface that’s used to manage and control Asterisk VoIP phone systems, particularly the Session Initiation Protocol (SIP) servers.
“Hacking SIP servers and gaining control allows hackers to abuse them in several ways,” the cybersecurity firm noted in its analysis. “One of the more complex and interesting ways is abusing the servers to make outgoing phone calls, which are also used to generate profits. Making calls is a legitimate feature, therefore it’s hard to detect when a server has been exploited.”
By selling phone numbers, call plans, and live access to compromised VoIP services from targeted businesses to the highest bidders, the operators of the campaign have generated hundreds of thousands of dollars in profit, alongside equipping them with capabilities…
http://feedproxy.google.com/~r/TheHackersNews/~3/Fe6gxKcIS9E/premium-rate-phone-fraudsters-hack-voip.html