
Cybersecurity researchers have taken the wraps off a new botnet hijacking Internet-connected smart devices in the wild to perform nefarious tasks, mostly DDoS attacks, and illicit cryptocurrency coin mining.
Discovered by Qihoo 360’s Netlab security team, the HEH Botnet — written in Go language and armed with a proprietary peer-to-peer (P2P) protocol, spreads via a brute-force attack of the Telnet service on ports 23/2323 and can execute arbitrary shell commands.
The researchers said the HEH botnet samples discovered so far support a wide variety of CPU architectures, including x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III), and PowerPC (PPC).
The botnet, despite being in its early stages of development, comes with three functional modules: a propagation module, a local HTTP service module, and a P2P module.
Initially downloaded and executed by a malicious Shell script named “wpqnbw.txt,” the HEH sample then uses the Shell script to download rogue programs for all different CPU architectures from a website (“pomf.cat”), before eventually terminating a number of service processes based on their port numbers.
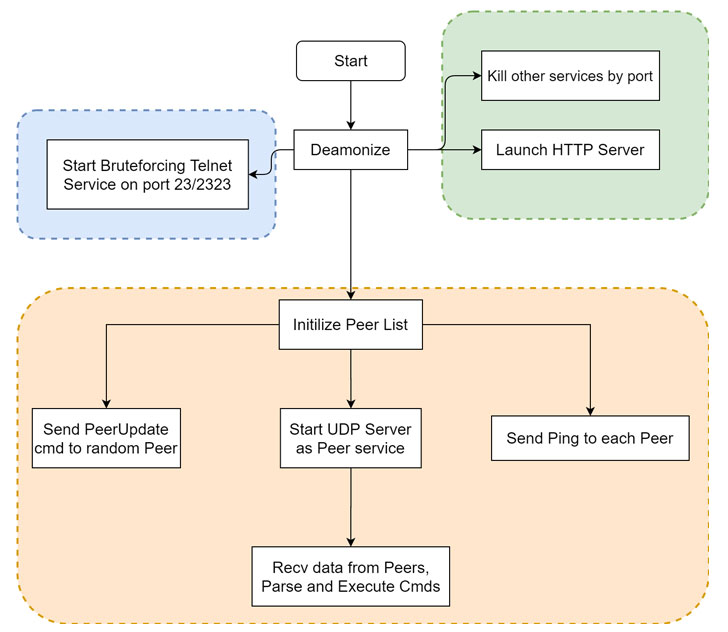
The second phase commences with the HEH sample starting an HTTP…
http://feedproxy.google.com/~r/TheHackersNews/~3/RPRZ_0DUWlE/p2p-iot-botnet.html












