An Iranian cyberespionage group known for targeting government, defense technology, military, and diplomacy sectors is now impersonating journalists to approach targets via LinkedIn and WhatsApp and infect their devices with malware.
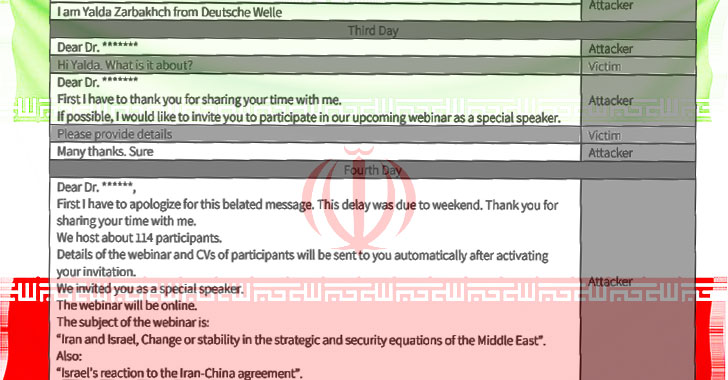
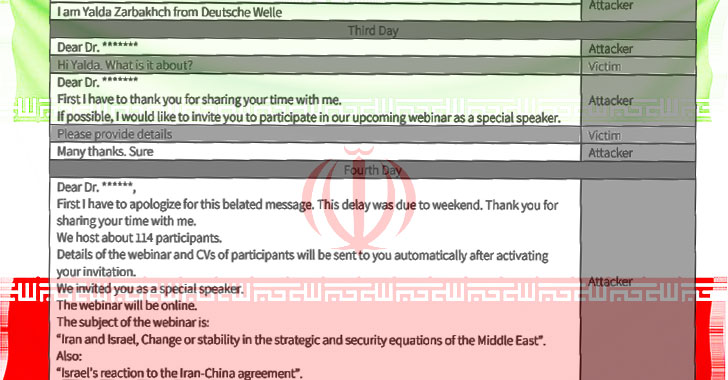
Detailing the new tactics of the “Charming Kitten” APT group, Israeli firm Clearsky said, “starting July 2020, we have identified a new TTP of the group, impersonating ‘Deutsche Welle’ and the ‘Jewish Journal’ using emails alongside WhatsApp messages as their main platform to approach the target and convince them to open a malicious link.”
This development is the first time the threat actor is said to have carried out a watering hole attack through WhatsApp and LinkedIn, which also includes making phone calls to victims, Clearsky noted in a Thursday analysis.

After the company alerted Deutsche Welle about the impersonation and the watering hole in their website, the German broadcaster confirmed, “the reporter which Charming Kitten impersonated did not send any emails to the victim nor any other academic researcher in Israel in the past few weeks.”
Charming Kitten (also known by aliases APT35, Parastoo, NewsBeef, and Newscaster) has been previously…
http://feedproxy.google.com/~r/TheHackersNews/~3/SlFF9FYAUqI/hackers-journalist-malware.html











