Cybersecurity researchers today uncovered a new strain of banking malware that targets not only banking apps but also steals data and credentials from social networking, dating, and cryptocurrency apps—in total 337 non-financial Android applications on it’s target list.
Dubbed “BlackRock” by ThreatFabric researchers, which discovered the trojan in May, its source code is derived from a leaked version of Xerxes banking malware, which itself is a strain of the LokiBot Android banking trojan that was first observed during 2016-2017.
Chief among its features are stealing user credentials, intercepting SMS messages, hijacking notifications, and even recording keystrokes from the targeted apps, in addition to being capable of hiding from antivirus software.
“Not only did the [BlackRock] Trojan undergo changes in its code, but also comes with an increased target list and has been ongoing for a longer period,” ThreatFabric said.
“It contains an important number of social, networking, communication and dating applications [that] haven’t been observed in target lists for other existing banking Trojans.”
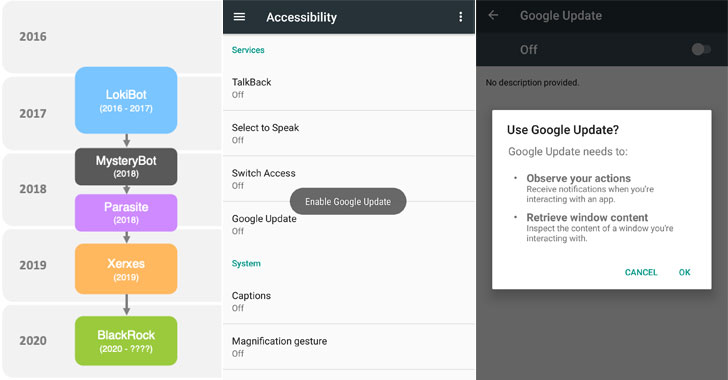
BlackRock does the data collection by abusing Android’s Accessibility Service…
http://feedproxy.google.com/~r/TheHackersNews/~3/qGGAlqCWJ6E/android-password-hacker.html