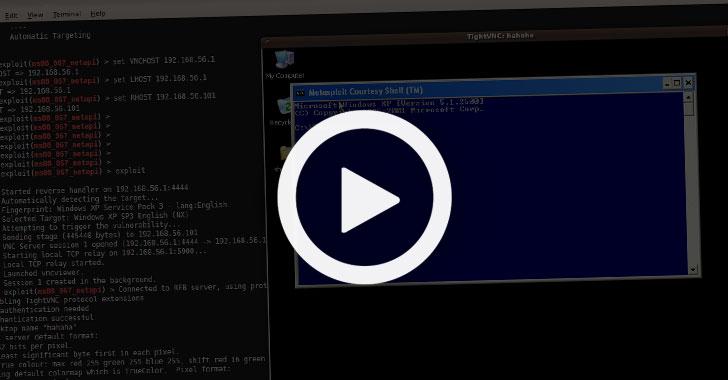
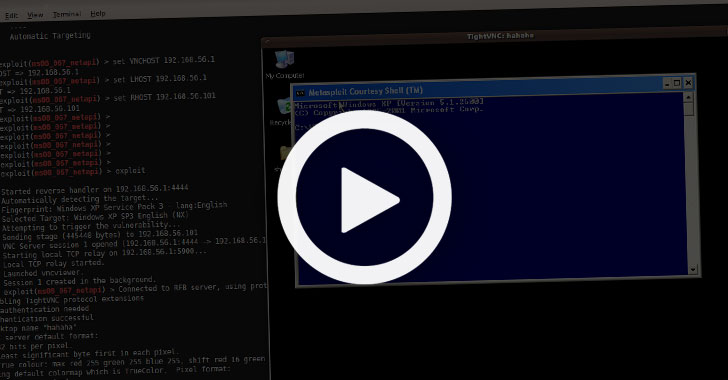
An OPSEC error by an Iranian threat actor has laid bare the inner workings of the hacking group by providing a rare insight into the “behind-the-scenes look into their methods.”
IBM’s X-Force Incident Response Intelligence Services (IRIS) got hold of nearly five hours worth of video recordings of the state-sponsored group it calls ITG18 (also called Charming Kitten, Phosphorous, or APT35) that it uses to train its operators.
Some of the victims in the videos included personal accounts of U.S. and Greek Navy personnel, in addition to unsuccessful phishing attempts directed against U.S. state department officials and an unnamed Iranian-American philanthropist.
“Some of the videos showed the operator managing adversary-created accounts while others showed the operator testing access and exfiltrating data from previously compromised accounts,” the researchers said.
The IBM researchers said they found the videos on a virtual private cloud server that was left exposed due to a misconfiguration of security settings. The server, which was also found to host several ITG18 domains earlier this year, held more than 40 gigabytes of data.
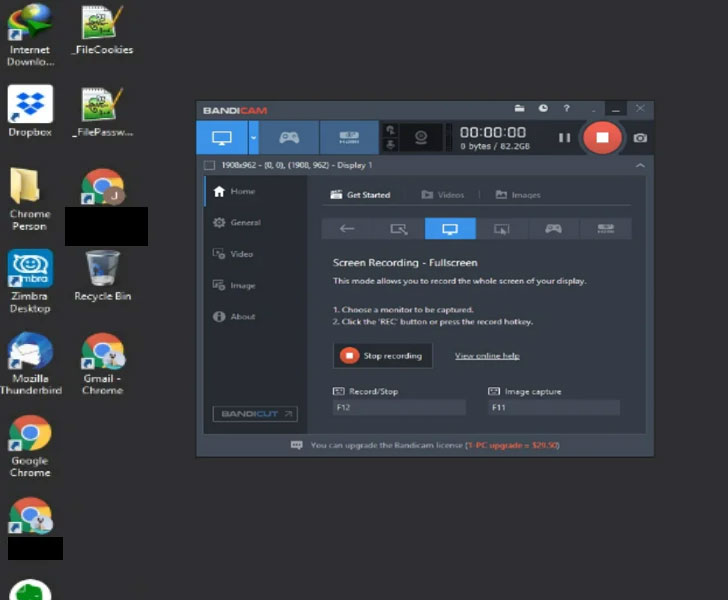
The discovered video files show that ITG18 had access…
http://feedproxy.google.com/~r/TheHackersNews/~3/AGojF6xrBSA/iranian-hacking-training-videos.html











