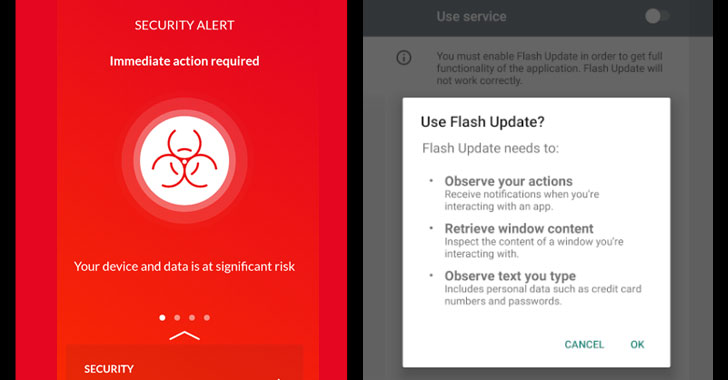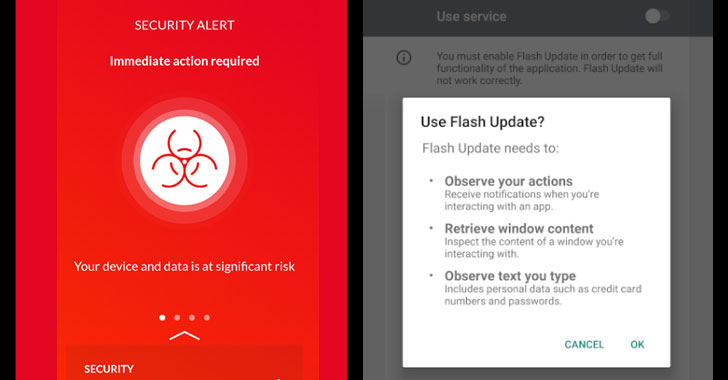
A new type of mobile banking malware has been discovered abusing Android’s accessibility features to exfiltrate sensitive data from financial applications, read user SMS messages, and hijack SMS-based two-factor authentication codes.
Called “EventBot” by Cybereason researchers, the malware is capable of targeting over 200 different financial apps, including banking, money transfer services, and crypto-currency wallets such as Paypal Business, Revolut, Barclays, CapitalOne, HSBC, Santander, TransferWise, and Coinbase.
“EventBot is particularly interesting because it is in such early stages,” the researchers said. “This brand new malware has real potential to become the next big mobile malware, as it is under constant iterative improvements, abuses a critical operating system feature, and targets financial applications.”
The campaign, first identified in March 2020, masks its malicious intent by posing as legitimate applications (e.g., Adobe Flash, Microsoft Word) on rogue APK stores and other shady websites, which, when installed, requests extensive permissions on the device.
The permissions include access to accessibility settings, the ability to read from external storage,…
http://feedproxy.google.com/~r/TheHackersNews/~3/EHR4BHQMwNo/android-banking-keylogger.html