
A new version of COMpfun remote access trojan (RAT) has been discovered in the wild that uses HTTP status codes to control compromised systems targeted in a recent campaign against diplomatic entities in Europe.
The cyberespionage malware—traced to Turla APT with “medium-to-low level of confidence” based on the history of compromised victims—spread via an initial dropper that masks itself as a visa application, the Global Research and Analysis Team at Kaspersky discovered.
The Turla APT, a Russian-based threat group, has a long history of carrying out espionage and watering hole attacks spanning various sectors, including governments, embassies, military, education, research, and pharmaceutical companies.
First documented by G-Data in 2014, COMpfun received a significant upgrade last year (called “Reductor”) after Kaspersky found that the malware was used to spy on a victim’s browser activity by staging man-in-the-middle (MitM) attacks on encrypted web traffic via a tweak in the browser’s random numbers generator (PRNG).
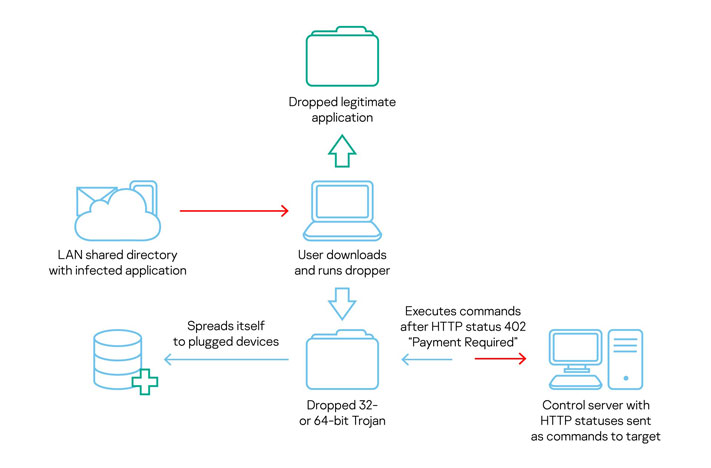
In addition to functioning as a fully-featured RAT capable of capturing keystrokes, screenshots, and exfiltrating sensitive data, this new variant of…
http://feedproxy.google.com/~r/TheHackersNews/~3/P0g3H2YLRTs/malware-http-codes.html












