
Cybersecurity researchers from ESET on Thursday said they took down a portion of a malware botnet comprising at least 35,000 compromised Windows systems that attackers were secretly using to mine Monero cryptocurrency.
The botnet, named “VictoryGate,” has been active since May 2019, with infections mainly reported in Latin America, particularly Peru accounting for 90% of the compromised devices.
“The main activity of the botnet is mining Monero cryptocurrency,” ESET said. “The victims include organizations in both public and private sectors, including financial institutions.”
ESET said it worked with dynamic DNS provider No-IP to take down the malicious command-and-control (C2) servers and that it set up fake domains (aka sinkholes) to monitor the botnet’s activity.
The sinkhole data shows that between 2,000 and 3,500 infected computers connected to the C2 servers on a daily basis during February and March this year.
According to ESET researchers, VictoryGate propagates via removable devices such as USB drives, which, when connected to the victim machine, installs a malicious payload into the system.
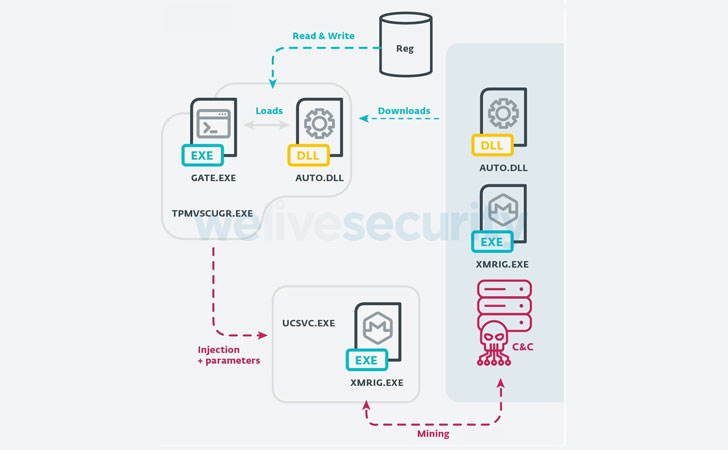
In addition, the module also communicates with the C2 server to receive a…
http://feedproxy.google.com/~r/TheHackersNews/~3/5uPgjiH-t0A/usb-drive-botnet-malware.html












