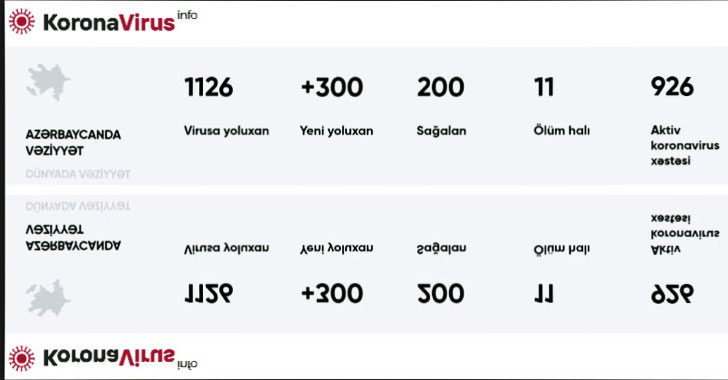
A new malware campaign has been found using coronavirus-themed lures to strike government and energy sectors in Azerbaijan with remote access trojans (RAT) capable of exfiltrating sensitive documents, keystrokes, passwords, and even images from the webcam.
The targeted attacks employ Microsoft Word documents as droppers to deploy a previously unknown Python-based RAT dubbed “PoetRAT” due to various references to sonnets by English playwright William Shakespeare.
“The RAT has all the standard features of this kind of malware, providing full control of the compromised system to the operation,” said Cisco Talos in an analysis published last week.
According to the researchers, the malware specifically targets supervisory control and data acquisition (SCADA) systems in the energy industry, such as wind turbine systems, whose identities are currently not known.
The development is the latest in a surge in cyberattacks exploiting the ongoing coronavirus pandemic fears as bait to install malware, steal information, and make a profit.
Using COVID-19 Themed Lures as Decoy
The campaign works by appending PoetRAT to a Word document, which, when opened, executes a macro that extracts the…
http://feedproxy.google.com/~r/TheHackersNews/~3/7yy74VqG4Ho/coronavirus-scada-malware.html











