Social engineering-driven malware threats continue to be a big threat, but new research details how cybercriminals profit off such schemes to launder hundreds of thousands of dollars from stolen credit cards of unsuspecting victims.
Cybersecurity firm Check Point Research, in a report shared with The Hacker news, uncovered the digital trail of a Nigerian cybercriminal, who went by the name of “Dton” and targeted hundreds of thousands of people under the moniker of “Bill Henry” by sending them malicious emails with custom-built malware.
The company said it disclosed the findings to concerned Nigerian and international law enforcement authorities for further action.
A multi-stage criminal scheme
The operation began with Dton buying stolen credit card details from Ferrum Shop, an online marketplace that sells over 2.5 million stolen credit card credentials, and then charging them each $550 each to fraudulently net more than $100,000 in illicit transactions.
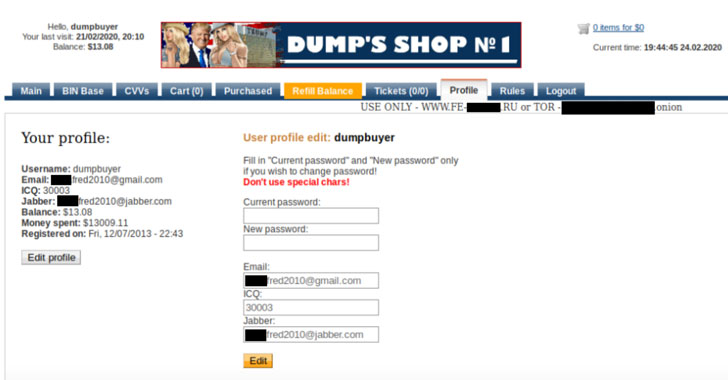
“During the years 2013-2020, the account he regularly logs into has been used to purchase over $13,000 worth in stolen credit card credentials,” Check Point noted.
Subsequently, the researchers found that Dton’s monetizing…
http://feedproxy.google.com/~r/TheHackersNews/~3/DOIyjfUjsuQ/nigerian-hacker-million-dollars.html