
It’s now or never to prevent your enterprise servers running vulnerable versions of Citrix application delivery, load balancing, and Gateway solutions from getting hacked by remote attackers.
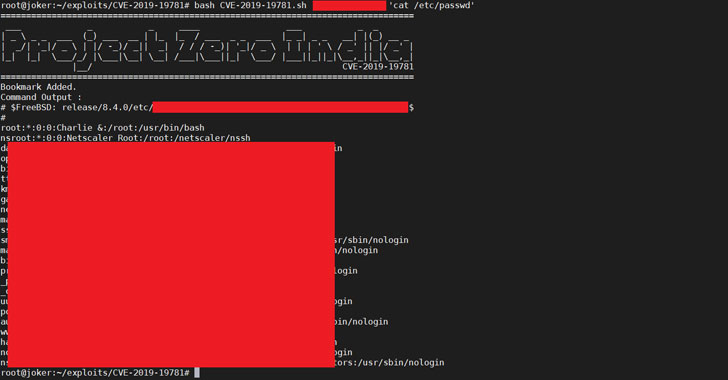
Why the urgency? Earlier today, multiple groups publicly released weaponized proof-of-concept exploit code [1, 2] for a recently disclosed remote code execution vulnerability in Citrix’s NetScaler ADC and Gateway products that could allow anyone to leverage them to take full control over potential enterprise targets.
Just before the last Christmas and year-end holidays, Citrix announced that its Citrix Application Delivery Controller (ADC) and Citrix Gateway are vulnerable to a critical path traversal flaw (CVE-2019-19781) that could allow an unauthenticated attacker to perform arbitrary code execution on vulnerable servers.
Citrix confirmed that the flaw affects all supported version of the software, including:
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler…
http://feedproxy.google.com/~r/TheHackersNews/~3/I8Tx34-GV64/citrix-adc-gateway-exploit.html












