Another day, another revelation of a critical unpatched zero-day vulnerability, this time in the world’s most widely used mobile operating system, Android.
What’s more? The Android zero-day vulnerability has also been found to be exploited in the wild by the Israeli surveillance vendor NSO Group—infamous for selling zero-day exploits to governments—or one of its customers, to gain control of their targets’ Android devices.
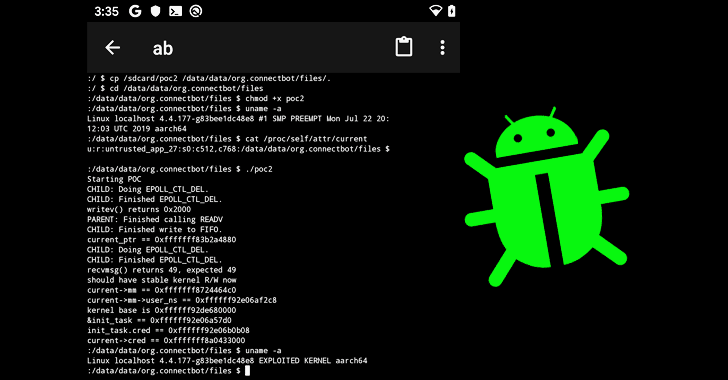
Discovered by Project Zero researcher Maddie Stone, the details and a proof-of-concept exploit for the high-severity security vulnerability, tracked as CVE-2019-2215, has been made public today—just seven days after reporting it to the Android security team.
The zero-day is a use-after-free vulnerability in the Android kernel’s binder driver that can allow a local privileged attacker or an app to escalate their privileges to gain root access to a vulnerable device and potentially take full remote control of the device.
Vulnerable Android Devices
The vulnerability resides in versions of Android kernel released before April last year, a patch for which was included in the 4.14 LTS Linux kernel released in December 2017 but was only incorporated in AOSP…
http://feedproxy.google.com/~r/TheHackersNews/~3/1XJRAKncBS0/android-kernel-vulnerability.html












